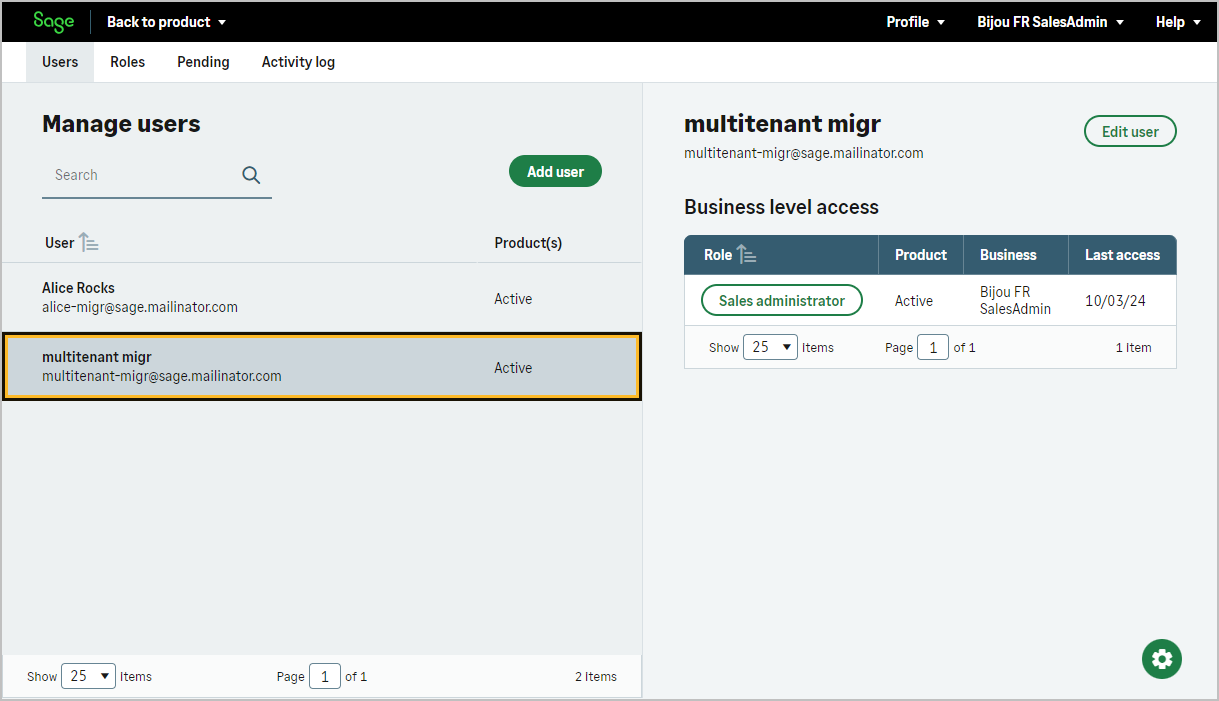
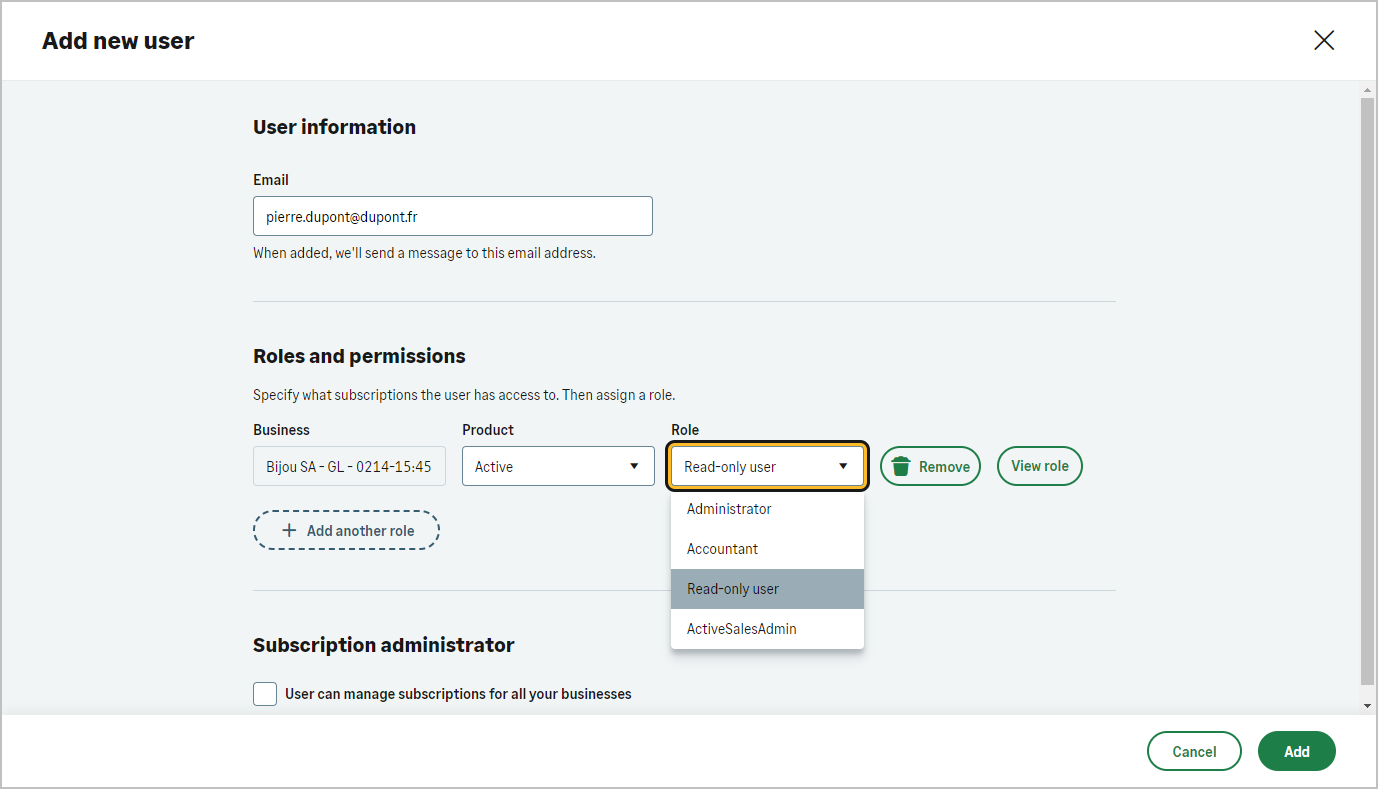
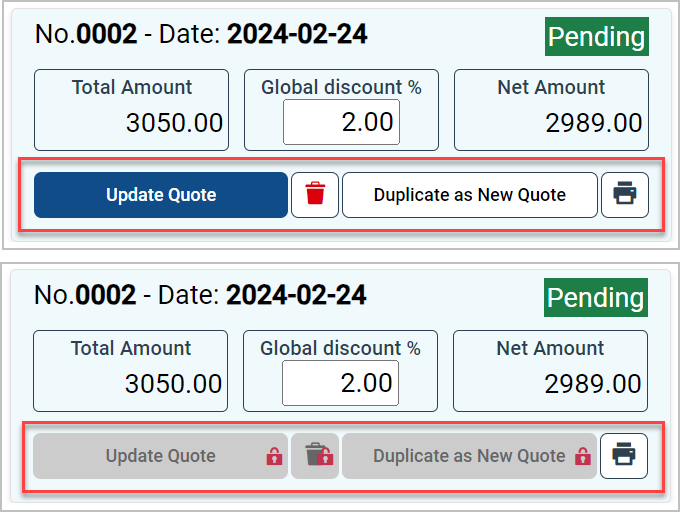
Users may have different roles based on their profile.
Details about individual users, such as authentication information and full name, are provided in the specific fields of this resource.
Additionally, each user has an associated application language, which defines their preferred language within the application.