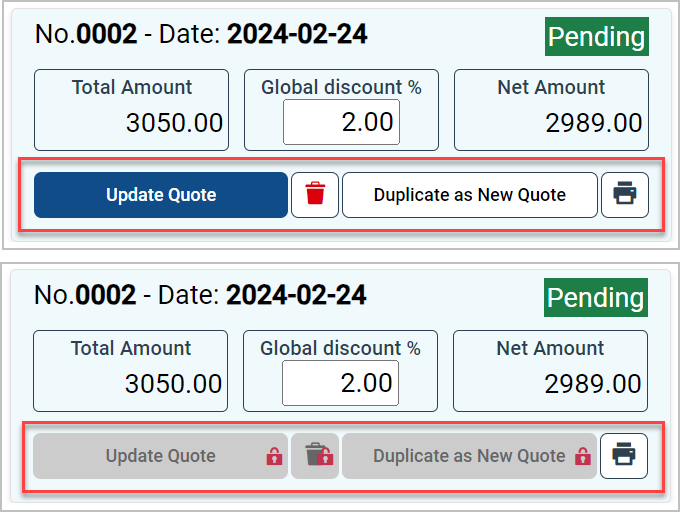
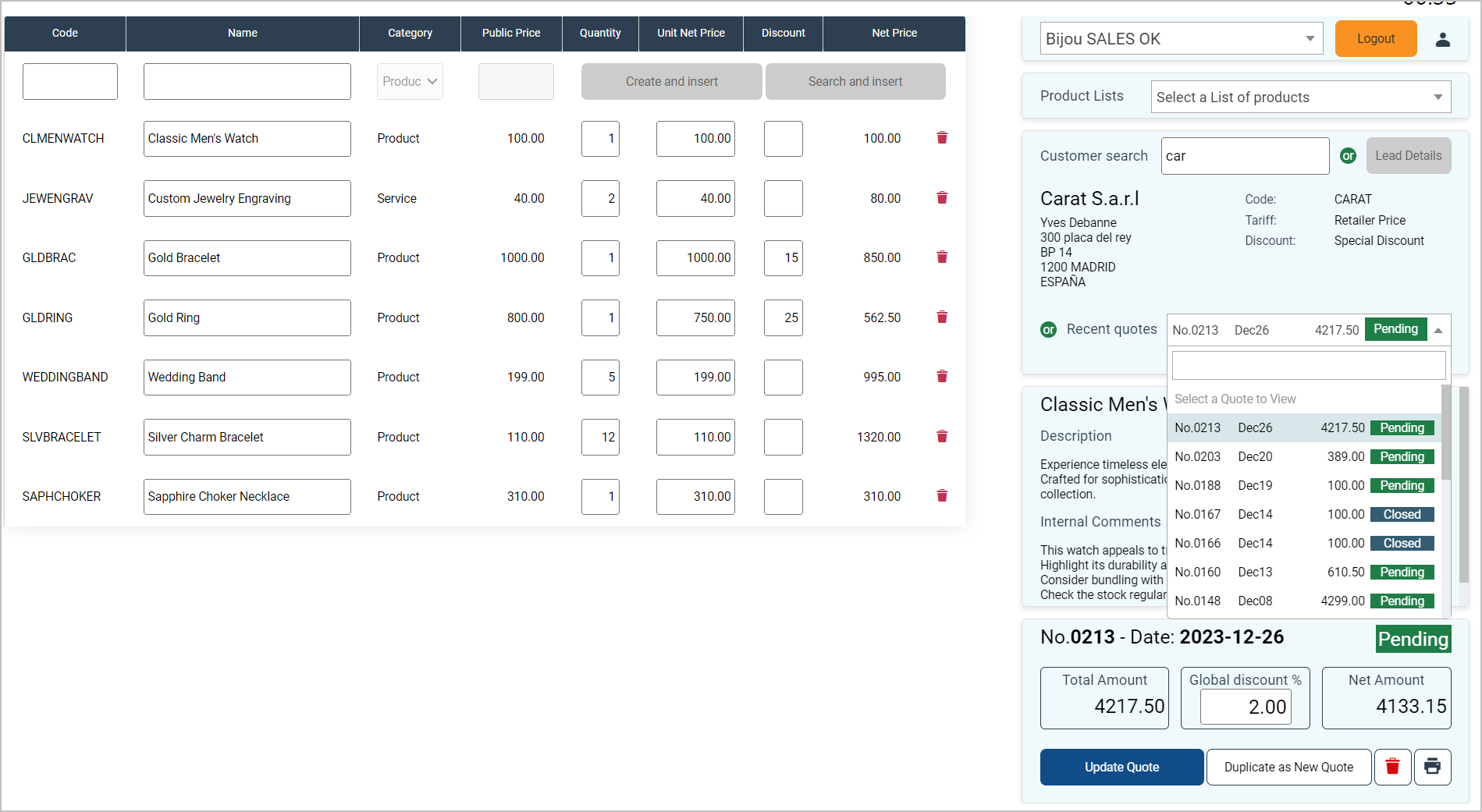
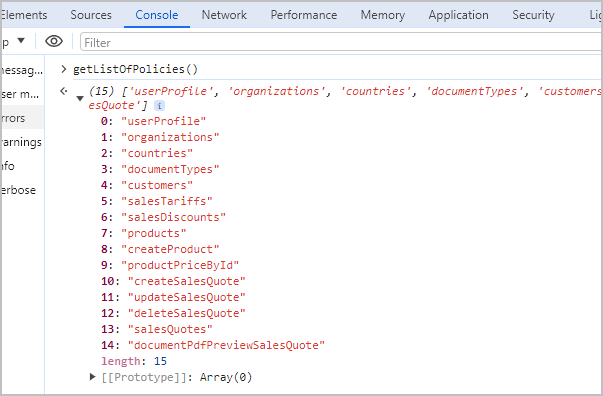
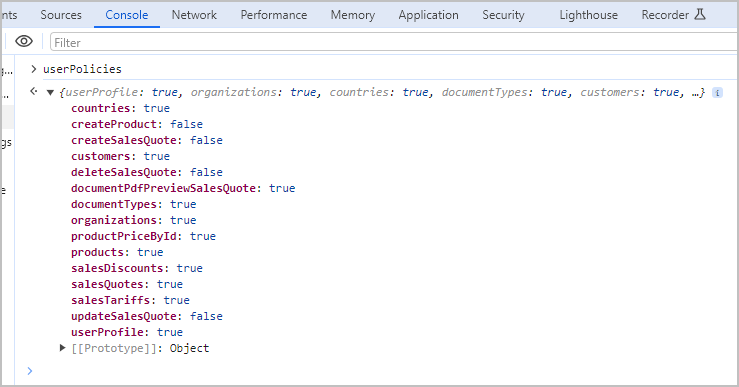
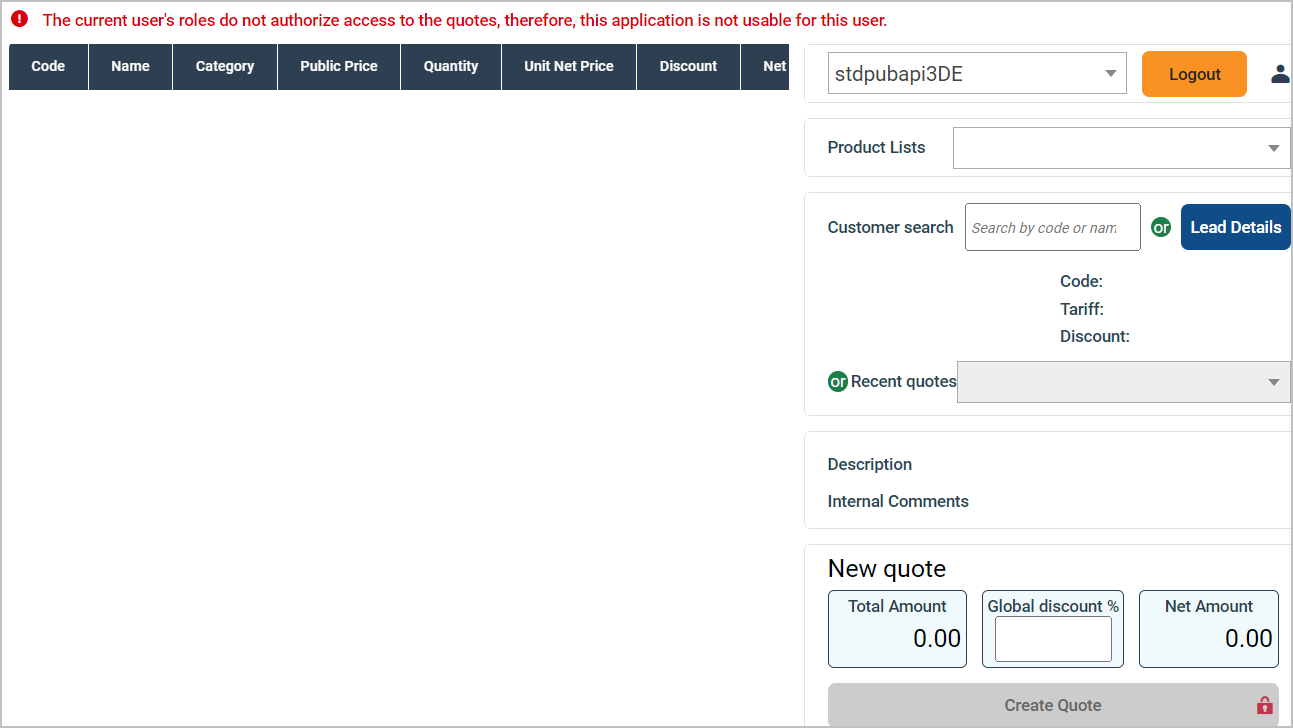
Furthermore, the Sage Active solution not only considers the user’s role but can also restrict access to certain data based on the Sage Active solution in use.
This service provides a mechanism to dynamically enable or disable features, or adjust the UI elements (like buttons or links), ensuring a tailored user experience that aligns with the user’s permissions.
See also: Key concepts / Users management